The most important thing in brief:
- PrintNightmare affects all common Windows operating systems, including older versions such as Windows 7, and remains relevant even in 2025 if patches are missing or point-and-print settings are not set correctly.
- Quick action is essential, such as disabling the printer spooler service on unused systems and applying Microsoft security updates (such as KB5004945) to effectively prevent attacks.
- Docusnap enables rapid identification of vulnerable systems and provides an overview of installed patches and running services so that companies can stay informed at all times and react efficiently.

“PrintNightmare” – What Is It?
PrintNightmare refers to a critical vulnerability in the Windows Print Spooler (CVE-2021-34527), originally discovered in mid-2021. It allows attackers to gain local system privileges, enabling them to install programs, read, modify, or delete local files, and even create new user accounts with full privileges.
Preventing a PrintNightmare Attack
This vulnerability has been actively exploited and can still pose a problem today if companies run outdated systems or fail to apply patches consistently. In large IT environments, it is still possible that some systems have the Print Spooler service enabled without actually needing it for daily operations. In addition, misconfigured Point-and-Print settings can lead to further attack scenarios.
What Can You Do About Microsoft PrintNightmare?
- Patch: Microsoft has released several updates to largely address this security hole. However, you should also ensure that Point-and-Print settings are correctly configured; otherwise, the attack surface may remain.
- Check the Print Spooler Service: Many organizations recommend disabling the Print Spooler service on systems that do not require printing. This helps reduce the risk of attacks.
- Regular Monitoring: Even though this vulnerability has been known for several years, some systems may still be operating without the latest patches. Ongoing monitoring is essential to quickly identify and fix security gaps.
Which Operating Systems Are Affected by PrintNightmare?
In addition to Windows 10 systems, all other older Microsoft operating systems have also been (and still can be) affected. For this reason, alongside the KB5004945 update for the latest Windows 10 version, Microsoft has released additional security updates specifically for older versions going back to Windows 7.
- Windows 10, Version 21H1 (KB5004945)
- Windows 10, Version 20H1 (KB5004945)
- Windows 10, Version 2004 (KB5004945)
- Windows 10, Version 1909 (KB5004946)
- Windows 10, Version 1809 and Windows Server 2019 (KB5004947)
- Windows 10, Version 1607 (KB5004948)
- Windows 10, Version 1803 (KB5004949)
- Windows 10, Version 1507 (KB5004950)
- Windows 8.1 and Windows Server 2012 (Monthly Rollup KB5004954 / Security only KB5004958)
- Windows 7 SP1 and Windows Server 2008 R2 SP1 (Monthly Rollup KB5004953 / Security only KB5004951)
- Windows Server 2008 SP2 (Monthly Rollup KB5004955 / Security only KB5004959)
Important: According to current information, installing the patch does not fully address the vulnerability if Point-and-Print restrictions are disabled or improperly configured.
Free Docusnap Report on PrintNightmare
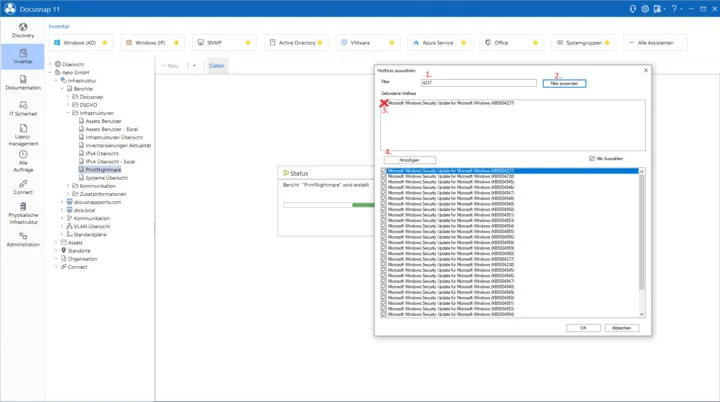
To help you quickly and easily check which systems in your network could be affected, Docusnap developed a special report back in 2021 that:
- Checks whether the Print Spooler service is running on each system
- Determines whether the respective PrintNightmare patch is installed
You can download this report for free from our website and import it into Docusnap. A detailed step-by-step guide is available in the German Docusnap Community.
Ongoing Protection against PrintNightmare with Docusnap
- Inventory Your IT Landscape: Docusnap automatically gathers all relevant information about your systems, including installed software and running services.
- Import the PrintNightmare Report: After importing this specialized report, you can analyze your systems for this specific vulnerability.
- Analyze the Results: The report provides a detailed overview of which systems are affected, whether the Print Spooler service is active, and whether the necessary patches have been installed.
- Take Action: Based on the results, you can take targeted measures, such as disabling the Print Spooler service on unnecessary systems or installing missing updates.
Summary
The PrintNightmare security vulnerability vividly demonstrates how crucial a continuous and comprehensive IT documentation strategy is. Even in 2025, PrintNightmare remains a relevant threat, especially for organizations running older Windows systems or failing to apply patches consistently. With the ongoing evolution of attack methods, it is essential to regularly check all systems, monitor the Print Spooler service, or disable it if not needed.
The next steps:
Using Docusnap, you can not only identify affected systems quickly but also initiate appropriate measures to effectively close security gaps. The tool supports you in inventorying and analyzing your entire IT landscape, keeping you informed of threats such as PrintNightmare. This way, your IT processes remain secure and efficient, even beyond 2025.
Try it for free


